In the year 2008, Satoshi Nakamoto, probably pseudo name of the person, conceived an idea for a decentralized e-cash system using Peer to Peer Network. In 2009, Satoshi published the founded idea as the article " Bitcoin OpenSource Implementation of P2P Currency" as a forum Post on a Website. Thus BitCoin a CryptoCurrency for P2P transactions is born.
The backbone of Bitcoin is Peer to Peer Network. Bitcoin is decentralized; no central server; no trusted third parties; Instead of trust, Bitcoin is built upon Crypto Proof. Hence it is called cryptocurrency. It is also a non-sovereign currency, as it is decentralized and not governed by the rules and values of any legitimate government for monetary value.
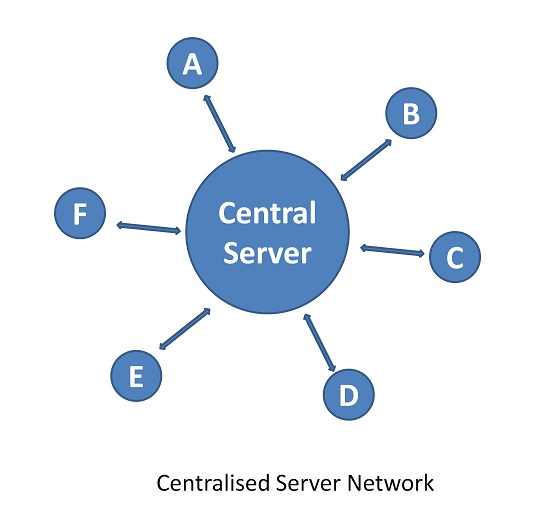
The Conventional Currency is monitored by the Central Bank of any Country (e.g. Reserve Bank of India). The Currency exchange between A and B happens via a centralized Server networked through various banks and the banking system. The trust is loaded on the Banks by the members, i.e. the citizens of the country. The Central bank becomes a third party between a transaction between A and B. This technology later got a generic name Blockchain Technology as it got recognition for new business models and applications.
Satoshi has attempted to create a money transaction system by eliminating a trusted third party and centralized Server. This money is the first CryptoCurrency Called "BitCoin" which is in use for International Business in addition to the sovereign currency.
Double Spending
Money being spent twice is called double-spending. Let us detail it with an example.
Mr.X goes to Café Coffee Day and orders Coffee. He pays the bill of Rs. 65 by physical cash and gets a receipt for the payment and also his coffee. This physical cash is now physically moved from Mr.X to Café Coffee day. This is a clean transaction.
On the other hand, if Mr.Y pays Rs. 65 by Digital cash (e-cash). Here is the hitch; the digital is not physical money. Like numbers in the Rupee note, digital cash has a digital signature as the identity. There is a possibility that the transaction can be rebroadcasted to one or more other beneficiaries and Mr.Y gets benefited by reuse of digital cash. Figure below, pictorially explains these scenarios of a double spend. This is Double Spending i.e the same money is utilized more than once and this is unethical.
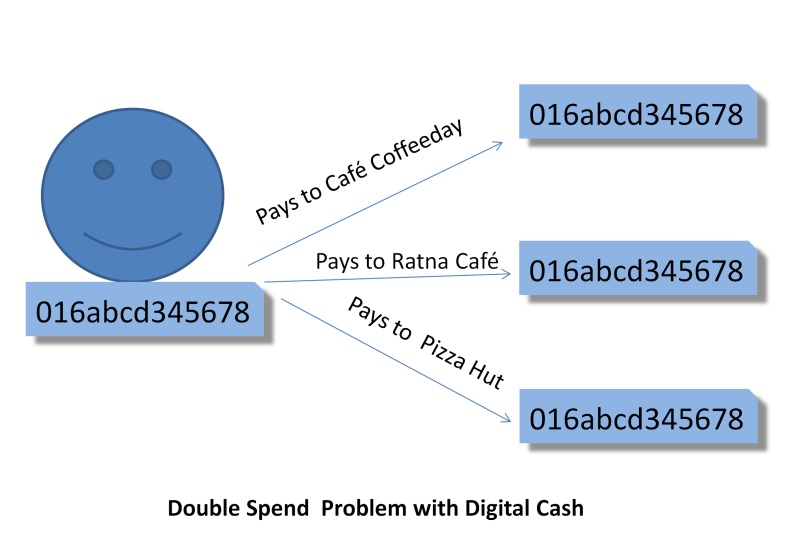
Double Spend cannot exist with physical cash but can happen with digital cash. This problem needs to be avoided and the possibility to be eliminated in the Digital Cash mechanism.
Bitcoin

Bitcoin is an Electronic Cash in purely operated in Peer to Peer network for the exchange of monetary value directly between members without the involvement of trusted third party like banks. Bitcoin is an e-cash system based on crypto proof as against the trust in sovereign currency transactions. Bitcoin is an e-cash digitally signed by the owner. A Bitcoin transaction happens by adding and hashing the previous transaction, encrypting with the public key of the recipient and time stamping it. Thus Bitcoin transactions are chained, irreversible, immutable, secure and authenticated. Bitcoin eliminates the double-spend problem.
Peer to Peer Network (P2P)
A network is a connection of computers and each computer is called a node. Generally, the network is formed by the member nodes and operates over the Internet. The characteristics and rules defined for the role and coordination amongst the nodes differentiate what type of network is it.
In Peer to Peer network, nodes are all equal like Peers, hence the name Peer to peer network. It is Distributed network architecture. The nodes are equally privileged and the tasks are distributed among the nodes. Files can be shared amongst the nodes without the need for the Central server. In a way, each node assumes the role of a server and client depending upon the task.
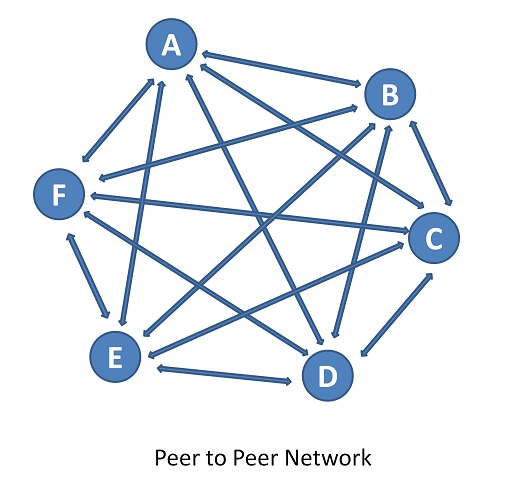
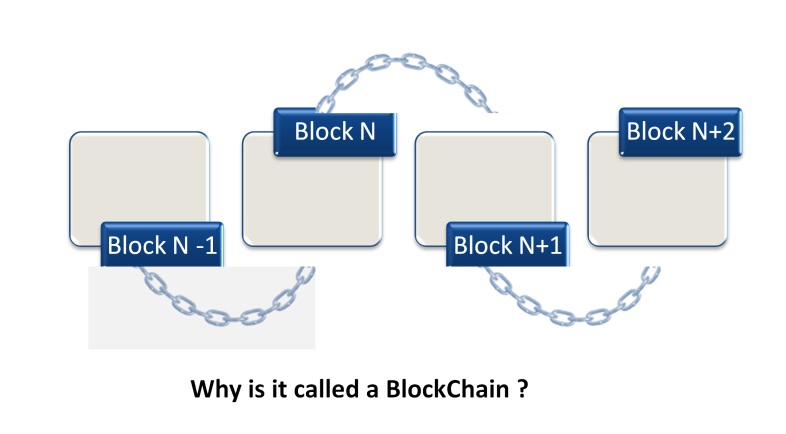
The concept of blockchain
Blockchain is a Universal Shared Distributed Ledger meant to keep a record of transactions of tangible and intangible digital assets. The transaction records are created as blocks to enhance traceability, trust, immutability, security, non-tamperable, accountability and transparency. These blocks are maintained as a chain in chronological order of creation. Hence this shared ledger is called Blockchain.
As the name suggests it is a ledger maintaining transaction records in synchronization with Peer node copy. It is distributed meaning it prevails in Network and operated on Distributed Network Architecture. The shared ledger is transparent because it is verifiable by the eligible members of the network. The blocks are encrypted making them secure. The blocks are timestamped to make them immutable and non-tamperable. Blocks are added in consensus with other nodes. This builds trust and eliminates the trusted third party. These characteristics of Blockchain Technology, make it favorable to Business enrichment cross the globe. The Blockchain technology is facilitated by technological advancements in Software engineering, Game Theory, Distributed Computing and CryptoGraphy (Sultan et al., 2018).
Blockchain technology could be applied to various business segments like Banks, e-publishing for protecting with Copyrights, Assets transaction, Manufacturing (Ex: to hold the history of the parts and process of a vehicle), Healthcare for holding patient history record, SupplyChain and Logistics management, etc.
Any transaction happens over the exchange of assets. For example, when you buy a car, you give money ( your asset) and get back a car ( a new asset form the dealer). Blockchain transactions can happen only over digital assets. i.e. assets have to be digitalized or digitally tagged to facilitate BlockChain transaction.
What is a Digital Asset?
A Digital Asset is anything that is a text or media in digital form (Binary form) and is enabled with the right to use. Simply a text or media is not a digital asset, because assets are transacted using the ownership rights.
Familiar examples are Photos made by artists, Publications by authors, websites, logos, etc. Although in digital form a, if not having rights associated with it it is not called digital assets. A photo possessed by you within your family is not a digital asset.
In today's world, everything goes digital. Hence it is important to convert it to be an asset to protect it. Further, the products traded over e-commerce are an example of digitalized assets, to enable them to be transacted over the virtual world for a physical transaction. Similarly, our Educational certificates can be converted into digital assets not only for protection but also for verification of qualification.
DigiLocker by Government of India is one such initiative. Internet of Things makes it possible to tag any immovable asset into a digital asset for transacting. Your house, your vehicle, anything can be tagged as Digital Assets. Thus digital assets help automate business processes. Blockchain increases the credibility of the business. Digital Asset Management has become a new business segment today.
Thus the new form of digital assets could be a Text/Media file or electronically tagged one.
Digital signature
A signature on a paper document is important to validate the content of the document and define the authority of the document. Similarly, a digital signature is required for electronic documents like a bank statement, Trade documents, Income tax documents and so on. A digital signature ascertains a person whom he claims to be, in an electronic document. A digital signature identifies the correctness of the sender and the integrity of the e-document. Digital signatures are equivalent to Signature and stamp on a paper document.
Digital Signatures can be created only by a complex mathematical process called "hashing" and cryptography methods. The communication of a digitally signed document uses Public Key Infrastructure (PKI) with a pair of Keys called Public Key and Private Key. The digital signatures are to be issued by Certifying Authorities called CA. The simplest process of digitally signing the document is shown in the figure below.
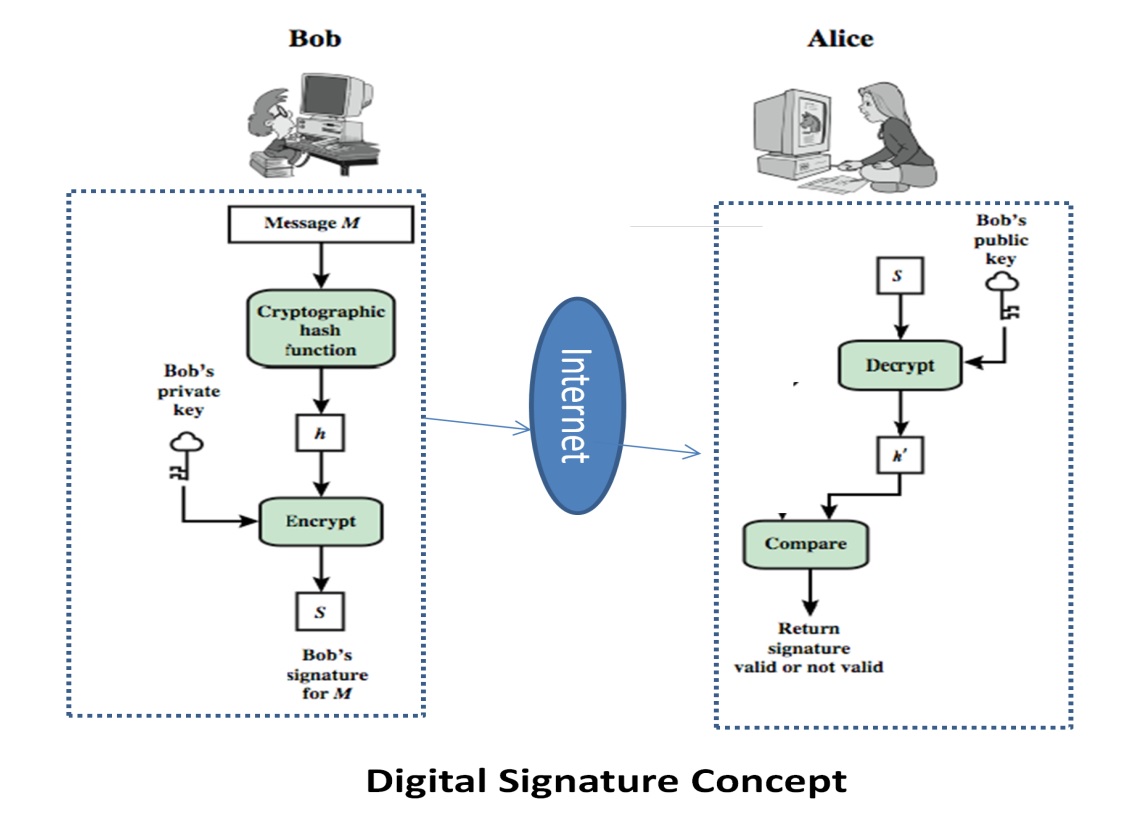
The Digital signature’s strength against attack depends on the length of the key and the encryption methods. The longer the key harder it is to crack. Digital Signature Algorithm (DSA), Rivest–Shamir–Adleman (RSA), Elliptic Curve Cryptography Algorithm (ECCA) are a few encryption algorithms.
References
Sultan, K., Ruhi, U., & Lakhani, R. (2018). Conceptualizing Blockchains: Characteristics & Applications. arXiv preprint arXiv:1806.03693.
