Just to recollect, Figure.4.1. is the picture representing the different network architectures. In a centralized system, important information is updated by the authorized central agency; for example, the transport office updates the driving license status, the international travel identity details are updated and maintained by Passport institution of a nation, banks maintain our financial transactions and so on. These agencies are also called trusted third parties. Since the centralized system is trust and authority based, there is no need for consensus.
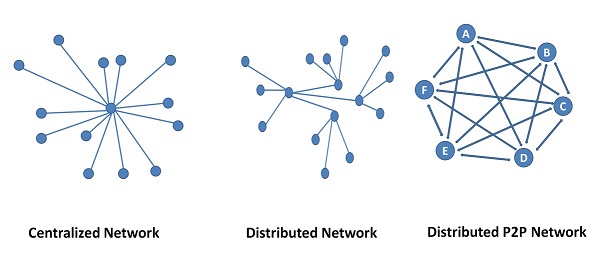
In a Distributed Network, transactions are executed in a distributed manner at various node locations. There is no central authority. So faith is posed on the nodes. However, issues like synchronization, correct functioning, nodes being alive and behavior of the nodes are issues. Nodes may intend to behave correctly but could be malfunctioning due to some failure in the node. Or there could be misbehavior due to planned attack like scenario. Hence a consensus mechanism is required to monitor the situation and ensure the health of the network is stable and usable.
The consensus is a fault-tolerant mechanism used in a distributed network to agree on a value or state of a process, as an agreement amongst the members of the network. This agreement happens based on the predefined set of rules and procedures. This set of rules and procedures that is to be followed is called consensus Protocol.
A Distributed Peer network is mostly anonymous. There is a possibility of the existence of Pseudonymous entities, simply to get disproportionate influence or votes for a winning scenario. This is called the Sybil Attack. This situation is to be avoided.
A Distributed network is a key functional requirement of Blockchain. And also, elimination of trusted third party; Public Blockchain operates as a decentralized, self-regulating peer network without single authority. The size of the network could run into a few hundred nodes or more. In such a scenario, the shared ledger needs a secure, reliable, functional, and efficient mechanism to ensure that the transactions occurring in the network are legitimate, genuine, trusted by all and integrity protected so that the transaction can be added as a block to the Blockchain. Consensus mechanisms and protocols take this place in BCT.
As we said, a consensus is created based on predefined rules and procedures which are called consensus protocols. Put in other words, Consensus protocols are about the nodes participating in the validation of transactions. There are few commonly used protocols in BCT like Proof of Work (PoW), Proof of stake (PoS), Delegated Proof of Stake (DPoS), Ripple and Tendermint, etc. Few other consensus mechanisms follow the principle of Byzantine Fault Tolerance (BFT) mechanisms.
Proof of Work (PoW)
PoW is the most commonly used algorithm in Cryptocurrency Blockchain. PoW requires the participating node to prove that the work is done and submit the proof as a solution to the puzzle. This proof qualifies the node to receive the right to add a block for the transaction to the Blockchain. Normally the proof of Work is about solving a mathematically hard puzzle solved using cryptography techniques. Whoever solves the puzzle first submits the proof and claims stake to add a block. This block, in the case of the Cryptocurrency system, is a cryptocoin like Bitcoin, Litecoin, Ethereum. This process is called Mining and is very heavily computational resource-intensive .i.e. requires long processing time and high energy consumption of the computers.
Proof of Stake (PoS
In this mechanism, the participating validator node should hold a certain percentage of stake in the network. This node is believed to have vested interested in keeping the network trustworthy. PoS is also a protocol used in Cryptocurrency systems. Thus majority stake means, holding more coins, instead of spending. This is a disadvantage to the concept of coin mining. However, it provides increased protection against malicious attack, as the attacker has to hold more coins than the validator. PoS is low cost, low energy demanding and an alternative to PoW consensus protocol.
Proof of Capacity (PoC)
The node having more memory and/or hard disk space is authorized to maintain the ledger and also mine the blocks.
Delegated Proof of Stake (DPoS)
This mechanism is also used in Cryptocurrency systems. A node can stake its coins to vote for a certain number of delegate nodes. The weight of the vote depends on the stake of coins. Delegate is a node that gets the authority to create /add a block to the Blockchain. Essentially, the delegate node has to get votes to get the power to add a block. The power is delegated by the other nodes using their coins stake as votes. Thus a delegate node becomes a trusted node. DPoS is the very fastest consensus protocol.
Multisignature
A Majority of the stakeholders, if not all have to agree that the transaction is valid. It is a simple mechanism used in It-enabled BCT applications. An example could be a sale of an asset; the conditions for sale are met by stakeholders like Registrar, Bank, Ownership Patta, Seller, buyer, etc.
Ripple Protocol Consensus Algorithm (RPC)
Ripple is also a Cryptocurrency. Ripple acts as a Central Currency in Cross border money transfer. i.e When Money is transferred from USD to INR, SGD to USD, etc. RPCA differs from other Cryptocurrency Consensus Protocols. Here each node in the Distributed network, maintains a Unique Node List (UNL). The consensus is expected to be obtained only from those nodes in the UNL list and not from all the nodes. UNL is a subset of the network and is collectively trusted against fraud in the network. Thus the network is Centralized /decentralized.
Tendermint
Tendermint is software that allows building an application over a Distributed network with security and replication features. Since the ecosystem is a distributed network, Consensus is essential. Tendermint ensures the correctness of replication while 2/3 of the network is voting for commit i.e when 2/3 of the network votes are received, the consensus is considered to be achieved. This also means that 1/3 of the nodes could be faulty or misbehaving and hence eliminated. Tendermint follows the Byzantine Fault tolerance Protocol. Tendermint allows Blockchain applications to be built over.
Byzantine Fault Tolerance (BFT)
BFT defines the tolerance of the network to a class of failures or problems in a Distributed network. Generally in a distributed network architecture is used in solving complex problems. Therefore lots of nodes are involved. It is to be noted that all nodes are working on the same or some part of the problem. In many cases, a fault-tolerant solution requirement is the main criterion for choosing a Distributed Network Architecture. Fault tolerance is required in Critical Systems Solutions. Not only the solution, but the correctness of the solution is also imminent. It is possible that in a network, few nodes may be misbehaving due to some kind of attack or malfunctioning due to genuine hardware failure. No matter whatever is the reason, the correctness of the solution is demanded. Hence voting happens; Majority wins is the scenario. What is considered as a majority is a question? A network is said to be dependable for its functioning when 2/3 of the nodes are in favor; even if 1/3 of the strength is not available; i.e. 2/3 majority is the minimum requirement for the network to be dependable. This condition is called Byzantine Fault Tolerance. Thus the consensus has arrived with a 2/3 majority.
In the absence of BFT, a node will be able to post malicious information, affecting the reliability of the network.
Practical BFT (PBFT)
PBFT is used as the consensus Protocol by IBM in its Hyperledger. PBFT comes with benefits like High Energy Efficiency, Transaction Finality and higher Rewards. Hyperledger is used as fabric for BCT in IT-enabled applications of BCT.
More about consensus algorithms
The other lesser-known Consensus Protocols are Leased Proof of Stake (LPoS), Proof of Identity (PoI), Proof of Importance, Proof of Elapsed Time, Proof of Burn and many more. Figure. 4.2. shows the usage of these consensus algorithms in various applications [1]. The numerical details are tabled in Table 4.1. Proof of Stake is the leading Consensus algorithm followed by Proof of Work and DPoS. There is one more interpretation to this is that the Distributed Ecosystem requiring Consensus algorithm mainly are categorized into two categories i.e. Cryptocurrency and IT-enabled Applications. PoS, PoW, and DPoS are mainly used in Cryptocurrency networks. The rest of the algorithms are applied mostly in IT applications. IT-enabled applications using Blockchain, have created many variants. Of these, PBFT and BFT have a slightly higher share. The data is as per 2018 December and published in [1].
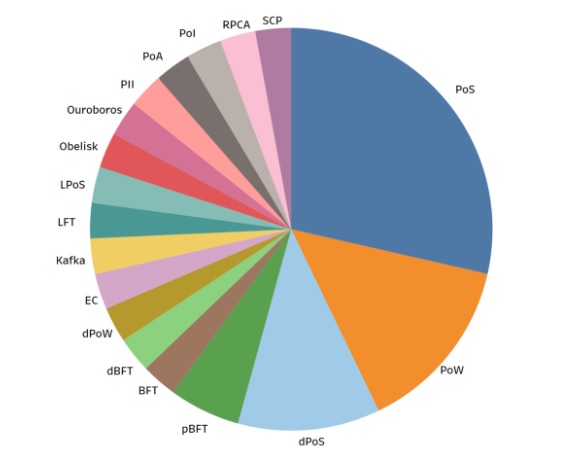
Usage share statistics of Consensus Algorithms
| Consensus Algorithm | % share in usage | |
|---|---|---|
| PoS | Proof of Stake | 28.57 |
| PoW | Proof of Work | 14.29 |
| DPoS | Delegated PoS | 11.43 |
| PBFT | Practical Byzantine Fault Tolerance | 5.71 |
| BFT | Byzantine Fault Tolerance | 2.86 |
| RPCA | Ripple Protocol Consensus Algorithm | 2.86 |
| Others | 34.28 | |
Summary of Consensus Algorithms
| Consensus Algorithm | Mechanism |
|---|---|
| Proof of Work (PoW) | Race to solve Math Problem |
| Proof of Stake (PoS) | Percentage of Tokens held is considered as the stake |
| Delegated Proof of Stake (DPoS) | Proportionate to Tokens, Token holder vote for the Delegates |
| Proof of Capacity (PoC) | Capacity to work or the capability of resources |
| Byzantine Fault Tolerance (BFT) | A 2/3 majority is required for consensus and to maintain a healthy network. |
| Practical BFT | As like BFT, but specific to IT Applications |
References
https://medium.com/@BlockTEST/whats-the-general-consensus-ab36d35a02e5 accessed on 4th Aug 2019.