A Model represents how the functional components of a system are interconnected in one's perception or for a purpose. A statistical model represents the patterns in data. An architectural modal represents the software design at the highest abstraction level. A class diagram is a model that represents the functional design of data structure or database components for a project.
Deriving an Architectural model is about identifying the design aspects to achieve the embedded characteristics, making use of the components of Blockchain. The embedded characteristics expected of a Blockchain Solution are Decentralization, Cryptography, Immutability, Provenance, Transparency, and Anonymity (Optional). The Components of a Blockchain Solution are:
- Nodes
- Transaction
- Block
- Chain
- Miners
- Consensus
The design aspects that are important in achieving these embedded characteristics are:
- The Blockchain Platform itself
- Distributed Ledger maintenance, The Consensus Process/protocol
- Access Control cryptographic requirements of the blocks
- The role of nodes and nodes discovery
- The transactions that make up a block
- The underlying network
Figure 5.1. is a typical layered architecture for generic Blockchain Application. The architecture could vary with specific to the use cases.
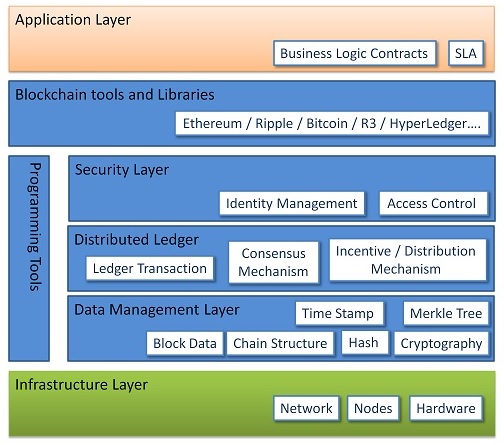
Application Layer
This layer has direct relevance to the Blockchain application. This is where the Requirements Specification, Service Level Agreement, UI requirements, Functional and Nonfunctional requirements are specified and are percolated as rules to the layers down. The Blockchain network operates as required by the application layer.
Blockchain tools and Libraries
Off- the- Shelf handy frameworks are always available for quick results, instead of starting from scratch. These Blockchain tools make available to the users, the required APIs, and libraries. These also provide an interface to set the rules and configure the network. Also, development tools are available for writing, documenting, testing, deploying and monitoring distributed applications. The purpose of the Library is to provide the intermediate code required. Bitcoin is a cryptocurrency Framework. Etherum and Ripple support both Cryptocurrency and Smart Contracts Blockchains. Hyperledger is an Open Source development tool from Linux Foundation for Business Solutions development.
Security Layer
This layer is essential in the case of Permissioned Blockchains ( both private and Hybrid). This layer handles the Identity Management of nodes and Access Control. Identity Management is about maintaining the digital identities of the nodes and their role. Access Control mechanism maintains a list of functions and/or data access that is available to each identity i.e.node. This helps manage the network in a role-based manner in a permissioned network.
Distributed Ledger
This layer has three sub-components namely Distributed Ledger, Consensus Mechanism and Incentivize / Distribution Mechanism. A distributed Ledger is storage. It has a written copy of the validated blocks in the append-only mode. It is this DLT which is available in a replicated and synced manner with all the member nodes. Consensus Mechanism, many options are available like PoW, PoS, DPoS, BFT, PBFT, etc. The chosen one for the network is implemented. The incentivize mechanism is specific to Cryptocurrency Networks. The nodes are either awarded the cryptocurrency or they are incentivized for the work done although the work is not completed first. The distribution system synchronizes the ledger and maintains replicated copies across the network.
Data Management Layer
This is the heart of the Blockchain network. A Transaction is the smallest building block of records that serves as a block in a Blockchain. The blocks get created based on the rules of the transaction. In smart contracts, the contract code is part of the transaction data. In the case of cryptocurrency networks, it is the puzzle that gets executed. The logic and code for hash generation, Timestamp, Merkle tree formation and the chain structure based on timestamp exist in this layer. Block is a data structure for storing a related set of transactions. Each block has certain data, Hash, Timestamp, Previous block hash, and Merkle root. Hash is generated using Cryptographic algorithms like SHA-256 and is a fixed length one. A chain is a sequence of Blocks in Timestamp order.
Programming Tools
The necessary to manage the security (IDMAC), Distributed Ledger Maintenance and Data Management layer functions are supported by the programming tools probably through applicable APIs. Programming languages like C++, C, Python, Java, and Ruby are handy for developing codes in these cases. Web development tools like HTML, CSS, Node JS are useful in User Interface development.
Infrastructure Layer
This layer has the physical and virtual resources of the Blockchain network. All nodes and the communication network along with the protocols are part of this layer.
Nodes
The nodes are the computers with an IP address and are users of the Application network. The nodes become a member based on the rule settings of the network. The nodes are underlying members executing and participating in all the functions of the Blockchain network. The nodes play various roles like Consensus participation, Execution / Initiation of Transactions, Writing on to the DLT if eligible, Accessing DLT at validator nodes, Peer to Peer communication. The nodes execute transactions, CPU intensive hashing, and I/O intensive network communication. DLT Storage requires a large storage space. Thus these nodes are heavily configured resources.

In a Permissionless public network, the nodes just join the network by simply having the protocol installed in it. But in the permissioned networks, governing rules get applied to become members. Based on the business intention, the nodes play a different role either as a member node or as a validator node as in figure 5.2. A member node can only initiate/receive transactions (Ex: a buyer or seller), whereas a validator node can do both initiate/receive transactions and as well participate in validating transactions ( Ex: a Bank, Transport authority, Licensing Authority, etc.). The validator nodes are also called Miners. All nodes will have the replicated copy of the Distributed Ledger.
The computational power of nodes is extremely heavy in Cryptocurrency networks. GPU, ASIC like high-end resource-efficient CPUs are used to help the miner solve the puzzle fast to claim the coin. Hashing is CPU intensive Job internal to the node.
Network
The network is a Distributed Decentralised network. This Network uses the Internet as a backbone for connectivity. The network is always I/O intensive to keep the communication synced amongst the nodes of the network. The network uses desired protocols for communication. An abstract model of the activities of the Infrastructure layer as described by IBM is pictured in Figure.5.3.

Concise Abstraction of Blockchain Application Model
Each Blockchain solution may have a unique approach, mainly because the Blockchain technology is still getting explored and evaluated for new and effective solution approaches, resource efficiency and framework stability. So, a generic-minimalistic-abstraction layer model is possible to be defined. Figure 5.4 shows the convergence of the 7 layers of Figure 5.1. into 4 layers model. The table below provides a clear picture of the functional focus of the layers and the workload corresponding to the function. It is to be noted this classification will never be possible to be physical but only virtual.

Blockchain Layers, Functional Focus, and Workload Summary
| Funcional Focus | Blockchain Layer | Workload |
|---|---|---|
| Contracts of the business | Application Layer | Any Business Solution |
| Language Compilers, Virtual Machine, Dockers, etc | Execution Engine ( Run time Environment) | Execution Engine ( Run time Environment) |
| Blocks Transaction, Indexing, etc. | Data Model | Analytics, I/O Heavy |
| PoW, PoS, PBFT, etc. | Consensus | Commits |

