BlockChain Generation
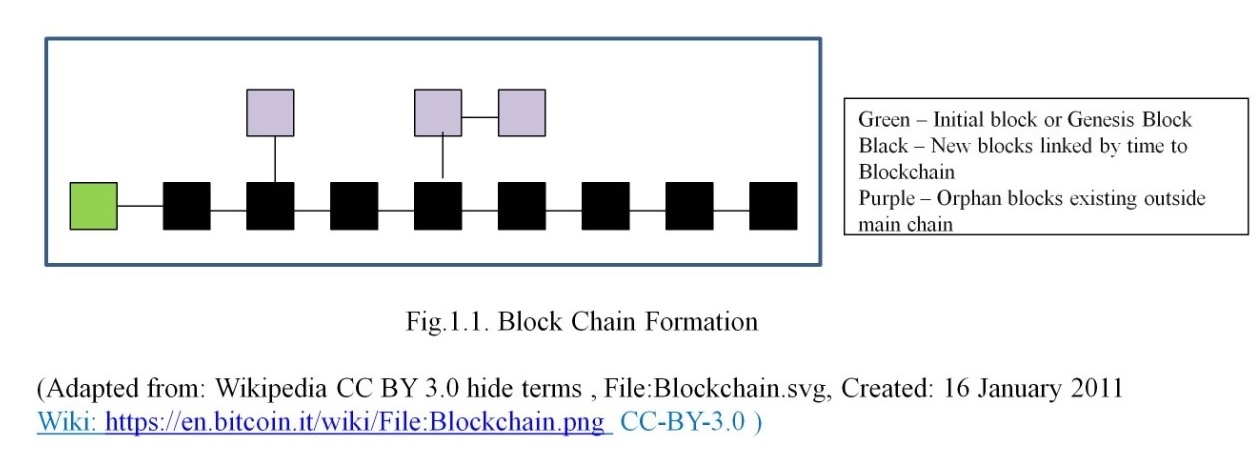
The transaction data are written as blocks. Each new block is chained to the earlier block, except the first block. Blocks are chained based on the chronology of timestamp. Blocks are added to the main chain only after obtaining consensus from the peer nodes. If no consensus arrived, those blocks get orphaned and stay away from the main chain. This activity of Blockchain formation is better explained in figure 2.1. The green square is the parent block or the first block. The ones in black color are the blocks in the main chain and alive. The purple ones are orphaned and discarded blocks.
Hashing
Hashing is a mapping operation of creating a shortcode for a stretch of string, using a mapping function. Generally used for generating a key or coding the original data. After hashing the data gets transformed. Such transformed value has many names like hash value, digest, hash code, key, etc., depending on the application. The function used in generating the hash value is called the hash function. It is a chosen function for mapping. The hash function is chosen keeping the three key characteristics in mind, i.e. Easy to Compute, Uniform distribution over the data and fewer collisions in the mapping process. Figure 2.2 shows the hash value generation with two different hash functions.
In DBMS, hashing used for generating Index, so that records can be accessed faster. In Blockchain, hashing is used for generating a cryptographic digital signature for the block. Blockchain uses fixed-length output hash. This means irrespective of the size of the transaction data, the hash output generated by the function is of a particular length as decided by the designer of the application. This concept makes hacking difficult thus enhancing security and immutability. Further, blocks can be easily located using the hash value as an index, as each block gets a unique hash. Hashing is a mapping function and a complex mathematical function. Hence hashing is computational resource intensive.

Nonce and Markel Tree
NONCE – An acronym for “Number only used Once”. In Cryptocurrency Applications, Nonce is a number added to the hashed block to meet the defined difficulty level of work. A nonce is a number, the miners of Cryptocurrency solve for and show proof of work in the network. In Commercial applications, Nonce serves the purpose of Token.
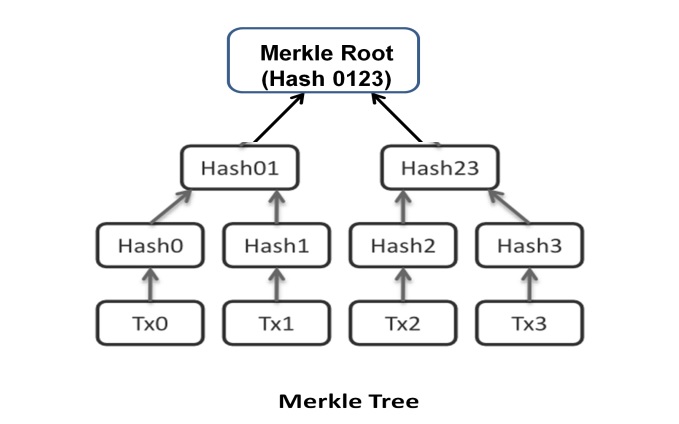
MERKLE TREE – It is a data structure also called Binary Hash Tree. Merkle tree is used to encode the Blockchain data efficiently and securely. Merkle tree allows the user to verify any particular transaction without having the necessity to go through the whole Blockchain. Thus Merkle tree enhances the efficiency of Blockchain. The Merkle tree diagram in Figure 2.3 provides a good understanding of its formation.
Blocks Formation
As seen from figure 2.4, a block in a Blockchain has four components, namely, Hash of the previous block, Transaction root value (Merkle root which contains the hash of all the transactions/records of the current block), Timestamp for block creation and the Nonce. Every new block is created with these four components and chained to the previous block. As blocks get added, the Blockchain grows. From figure 2.4, it can be inferred that only new blocks can be added and chain cannot be broken. Already created blocks cannot be altered. If ever such a necessity arises, such modifications will have to be done by way of new transactions satisfying the necessitated corrections. This characteristic is called non-tamperability.

It is to be noted that the definition of a transaction is "Unit of Work". Work is done in many steps of sub-transactions. These sub-transactions form the leaves of the Merkle tree. The depth of the Merkle tree depends on the number of leaves. A hash is generated for each leave. Each two hash is rehashed at the next level until the root is reached. The Merkle root is the mother of all hashes in the block.
Note that the hash of the previous block is one of the components for current clock formation. This ensures immutability. i.e no block can be inserted out of order. Timestamp provides verifiability that the blocks are in chronological time order. Nonce ensures that the work defined is done. Merkle root packages the sub-transactions securely using an overall hash.
Thus Blockchain inherits the characteristics of Security, Immutability, Traceability, and Verifiability. These characteristics of Blockchain increase the trust in whatever is done. Further, a group of individuals who have never met could do business online, cooperatively in a system that is inbuilt with trust against cheating.
Database Vs. Blockchain Technology Transactions
We have been discussing transactions for a while. Nobody can fail to recollect transactions of DBMS. Therefore a comparison between DBMS operations and Blockchain Operations is done here. But one has to remember that the data handling methods are entirely different approaches between the two and neither one is to replace the other. A Blockchain may be a database but a database is not a Blockchain.
| # | Traditional Database Transaction | Blockchain Transation |
|---|---|---|
| 1 | Data is maintained as records | Data is inbuilt into the blocks |
| 2 | Create, Modify, Update and Delete are operations that can be carried out by clients on Database. Read / Write feasible on any record | Blockchain is append-only structure. A block created becomes a read-only block; write operations feasible only for new block creation. |
| 3 | Operates on Centralised Client / Server Concept. The users are called Nodes/ Clients. | Operates on Peer to Peer Decentralised Network architecture. All nodes are generally equal. |
| 4 | Centralized Ledger | Distributed Ledger |
| 5 | With Authentication, a client can modify data in the Database. | Any addition requires voting by peers |
| 6 | A Designated authority authenticates client credentials. If any compromise happens in the authority, data may also be compromised. | Peers do verification and validation. This consensus mechanism makes it difficult to tamper data. |
| 7 | Designated authority is the administrator | Most of the nodes participate in the administrator role. |
| 8 | DBMS software is accountable for the Integrity of the Database. Transparency is a user's rights-based issue. | Public verifiability provides integrity and transparency |
| 9 | Database meant for data handling | Blockchain is more suited for process orientation i.e. when the process of transaction is more important |
| 10 | DBMS provides snapshot almost to a moment | Blockchains provide status “now” and maintain an archive |
| 11 | Difficult to trace how the changes to a record have happened | Write to a block is Possible to be verified at any time |
The lifecycle of Blockchain Transaction
Let us analyze the steps involved in a blockchain transaction with an example. Let us say B sells his Bike to A. A, B, RTO office, Insurance Company, Banker are members of the Blockchain application network. The chronological steps involved in the transaction and block creation are:
- B puts up his terms of sale for Bike.
- This is created as a block n and broadcast to all members
- A shows his interest to purchase bike along with his price bid
- The banker validates A’s bank balance
- The RTO validates the ownership of B over the Bike
- The Insurance Company confirms the life of bike insurance
- When all have approved, the money gets transferred from A to B
- Money added to B’s account
- The digital contract for Sale created
- A confirms receipt of Vehicle
- Records newly created at RTO of new vehicle ownership
- Insurance company changes the name of the owner
All the above steps get into a block as transaction details. The sequence essentially depends on the set rules for transaction and block creation. Hence the sequence of sub-transactions may vary from application to application. Finally, the block is created and added to the chain. We call this as the life cycle of a Blockchain transaction. The simplicity here is that everyone involved is part of the network and the bike sale happens with full transparency.
If the same bike sale has to happen over a non-blockchain model, we know the hassles and run around one has to go through all the third parties and the time required along with the stress. The risk and stress are in getting the ownership document verified, the insurance details verified for the claims, the financial status of A getting verified. Explaining those steps is outside the scope here.

